
- attack scenarios

- Download without defense
Description:
Many application systems or components provide file download functions, such as downloading templates, executable files, etc. If the background code is not filtered, you can directly use directory jumpers (such as../ or..\) Changing the file download path allows the arbitrary download of files from the server (such as source code, configuration files and other sensitive information files).
Test method:
First, look for all links that can download files. For example, you can catch the following links, such as 127.0.0.1/test/test.php? file=test.png, pay attention to the value test.png of the file parameters (most names are filename,page,javascript:open, etc.), which is obviously directly associated with a static resource. If the background code is not filtered, you can download any file on the server through directory jump, such as the passwd file on the Linux system, the boot.ini file on the windows system, the website source code, etc.
For example:file=../../../../ etc/passwd
Other test methods:
Truncate read files../../../../ etc/passwd.jpg
File name bypass modifies the file name in the request message The requested URL/upload/supplier/.../.../.../was not found on this server. etc/passwd
2.Bypass download defense mechanisms
Description:
Some background code filters downloaded files, but it is not rigorous, only filters../ or..\ etc., at this time you can bypass it through various coding changes.
Such as:
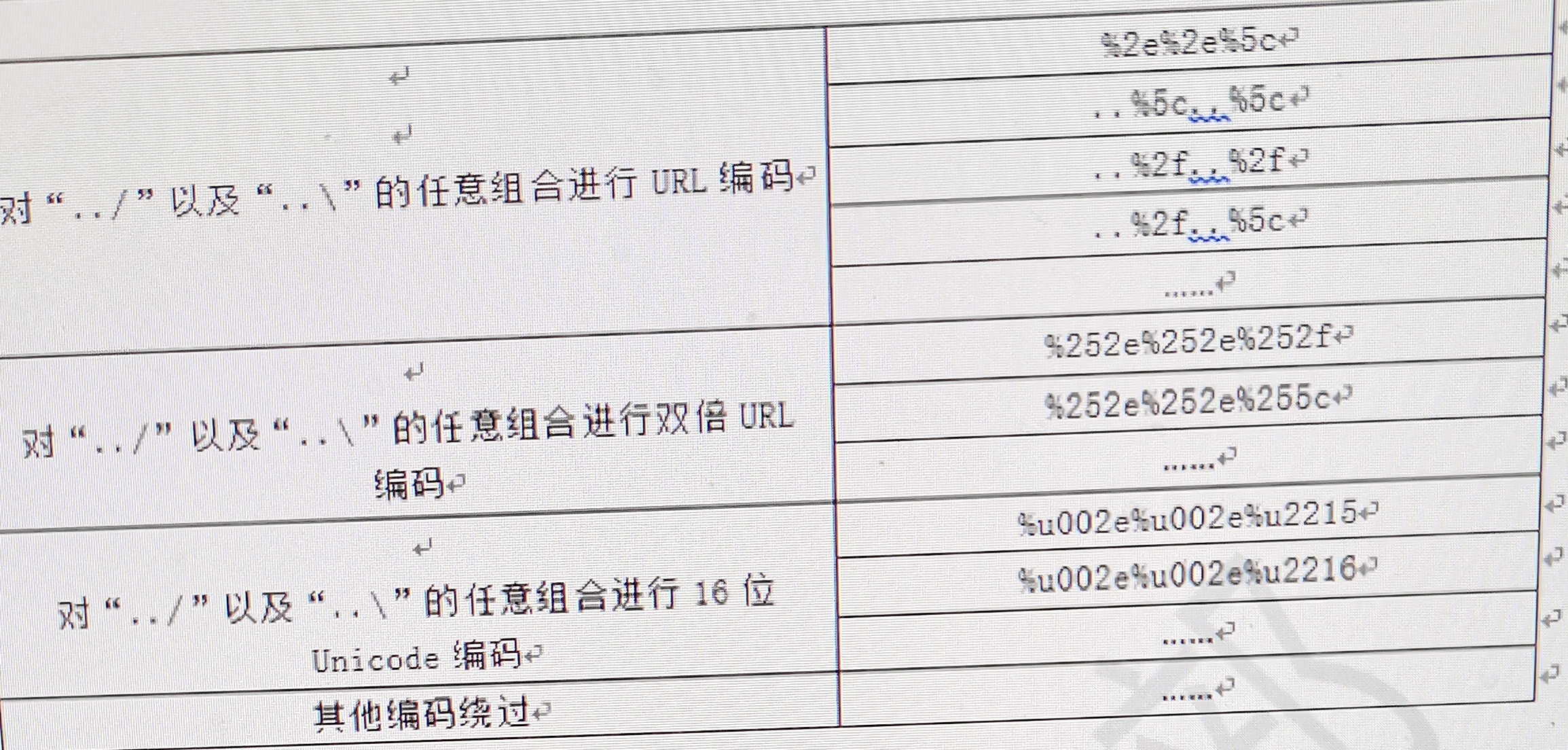
- impact
This may cause attackers to arbitrarily download server files, application system code, etc.





Comments0